
There's an old adage that humans are the weakest link in cybersecurity – but they can also be one of the strongest links if they're able to identify security risks.
Google's parent firm Jigsaw has come up with one way of helping people hone their phishing skills. It devised an eight-question quiz in which people must differentiate genuine emails from fake ones.
It may not be as easy as many people think – after the participant selects an answer, the quiz then offers a ‘show me' option that explains exactly why the example would be genuine or fake.
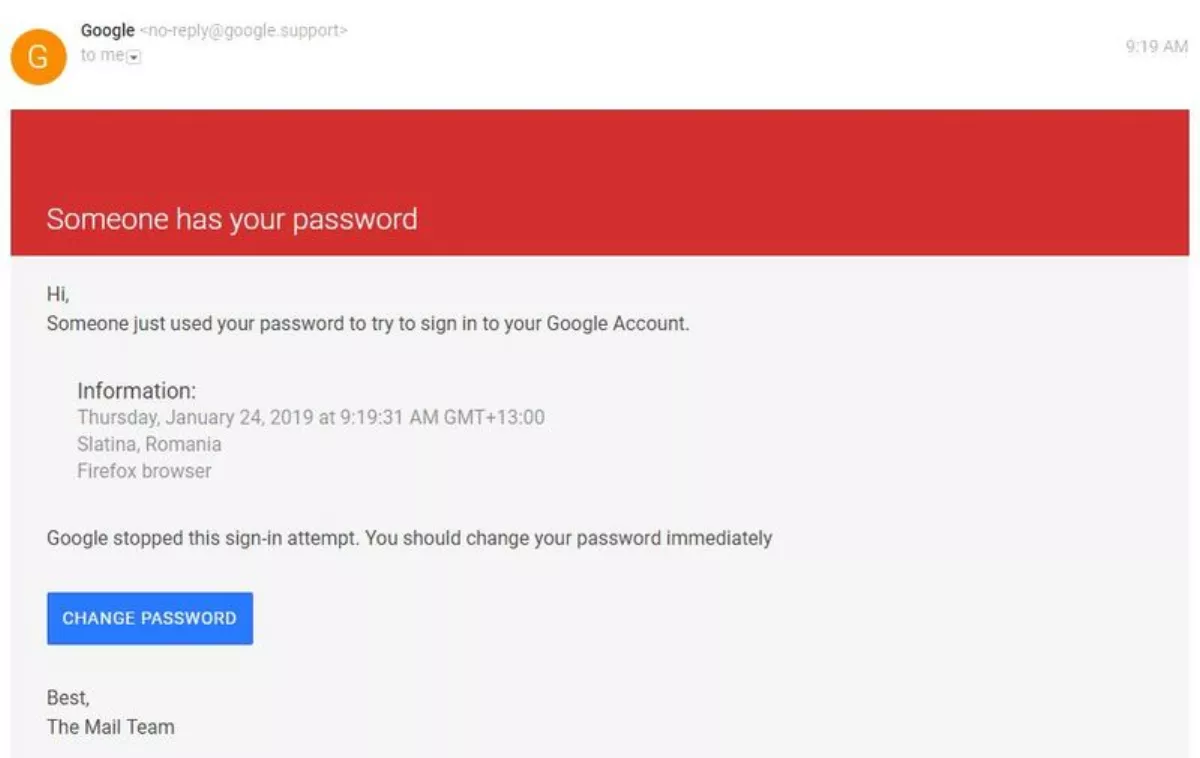
The examples include document shares appearing to be through Google Drive, links to downloads from fax machines, Dropbox notifications, Google logins, permissions requests, and more.
According to Jigsaw, “We created this quiz based on the security trainings we've held with nearly 10,000 journalists, activists, and political leaders around the world from Ukraine to Syria to Ecuador. We've studied the latest techniques attackers use, and designed the quiz to teach people how to spot them.
There's undoubtedly a need for more training simulations like this one – Symantec's 2018 Internet Security Threat Report found that 71% of all targeted attacks started with spear phishing to infect victims' systems.
F5 Networks' 2018 Phishing and Fraud Report presented similar findings – 71% of phishing attacks between September 1 2018 and October 31 2018 impersonated 10 high-profile organisations. The report also said that phishing was the root cause in almost half of the breach cases F5 investigated.
No matter which statistics you dig up, the message is almost the same: phishing emails are still sent by the masses, and they're still tricking people.
“Some of the most famous examples of hacking and cyber-theft began with phishing. In 2016 hackers affiliated with the Russian intelligence services sent a carefully crafted spear-phishing email to John Podesta, Hillary Clinton's campaign manager, and (because he didn't have two-factor authentication enabled) they gained access to his email account,” says Jigsaw.
At the end of the quiz, Jigsaw helpfully redirects participants to a page that encourages people to turn on two-factor authentication (it's a genuine request).
“When you have two-factor authentication enabled, even if an attacker successfully steals your password they won't be able to access your account. We also offer a Chrome extension called Password Alert that protects you from entering your Google password in a fake login page,” says Jigsaw.
Try the quiz at https://phishingquiz.withgoogle.com/.
