
Addressing real-world security challenges with a touch of a finger
Fingerprint technology is a mature, proven method for user authentication across a range of industries, use cases and environments.
Selecting the right fingerprint technology often comes down to the level of security and match accuracy required, the capabilities and features needed, and the usability to achieve both adoption and productivity.
Why fingerprints
The fingerprint is one of the most widely used methods for biometric authentication due to its speed, ease of use, high level of accuracy and cost-effective nature.
Fingerprints possess several unique features that make them valuable for various applications.
Firstly, they are universal, meaning almost everyone has them. Secondly, each person's fingerprint is unique and distinguishable, making it an excellent identifier. Additionally, fingerprints are reasonably stable and permanent, remaining consistent over time. They are also easily collectible, as they can be acquired, measured and processed with ease.
Moreover, fingerprints are defendable, meaning they can be protected from abuse, misuse, theft, imitation and substitution. When combined with recognition techniques, fingerprints are highly performant, offering accuracy, speed, scalability and ease of use across various applications. They are also adoptable, with the highest adoption rate for biometric authentication, according to an industry report.
The three elements of fingerprint biometric systems
A fingerprint biometric system consists of several components which work together to make an effective solution.
The process begins with the fingerprint sensor, specifically designed for the capture and preliminary processing of fingerprint data. Subsequently, a biometric algorithm is employed to extract minutiae data from the fingerprint, which includes details like ridge endings, ridge bifurcations, ridge islands, minutiae orientation, and various measurements.
Additionally, a presentation attack detection (PAD) technique may be implemented during the fingerprint capture to verify the authenticity of the fingerprint, ensuring that it originates from a living person.
If the predetermined conditions are satisfied, the digital fingerprint dataset is then securely stored as a record known as a template within a cryptographically protected storage enclave.
When a matching operation is required, the presented fingerprint undergoes a re-evaluation for liveness, and the corresponding template is retrieved from the secure storage for the matching process to take place.
The following are three important factors to consider when identifying an optimal biometric authentication system from a low-performing one:
- How well the capture works for a range of fingers, skin types and print conditions across different environmental conditions such as temperature, humidity, light, surface oils, dust and dirt,
- How effective PAD works in identifying and rejecting fake finger attempts and
- How well the system can accurately match legitimate users while rejecting illegitimate users.
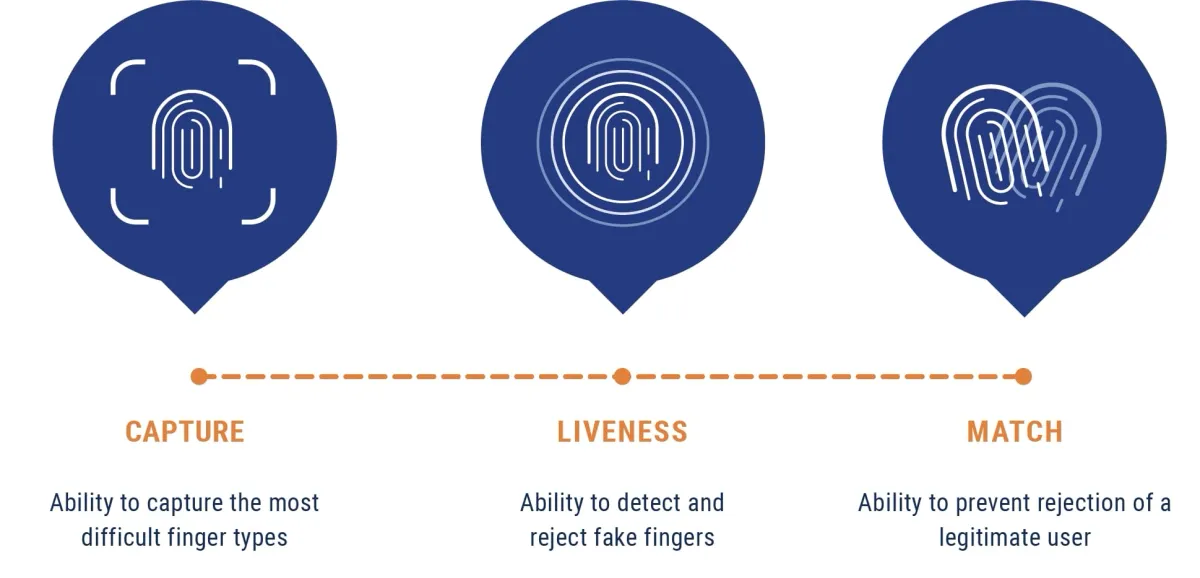 The Three Elements of Fingerprint Biometric Systems
The Three Elements of Fingerprint Biometric Systems
Key considerations for selecting the right fingerprint technology
The key considerations and requirements for selecting fingerprint technology boil down to a balance between the total cost of ownership, security, suitability and usability.
Security:
- Is the industry highly regulated, such as financial services, healthcare, government entities or law enforcement?
- Are advanced capturing and biometric authentication specifications mandatory?
- Is there a need to ensure anti-spoofing?
- Is there a need to have endpoint security so networks, systems and data behind the firewall won't be impacted in the case of the fingerprint device being hacked?
Suitability:
- Will the technology be embedded in devices that require low power, battery-operated capability and portability?
- Will the technology need to fit into small spaces or be used in difficult elements or environments, indoor or outdoor?
- Is durability from unpredictable weather and lighting conditions a factor?
- What applications will the technology be used for, such as mission-critical border control or more common commercial use?
Usability:
- Does the technology perform capture and matching with ease and consistency?
- Does the technology need to handle high volumes of fingerprint captures and matches?
- Is matching quick and accurate to enable user productivity instead of friction frustration?
- Will the device be used by multiple people in a shared workstation setting?
- Can the reader handle all types of fingerprints and diversified demographics for the mass population?
Based on the above criteria, organisations can decide what kind of fingerprint capture technology best fits their deployment.
For example, for a shared environment with limited space, such as healthcare clinician's terminals, a slim and durable capacitive sensor would be a good fit. For more demanding use cases in highly regulated, mission-critical environments that can't risk an identity misstep, such as banking or border crossing, organisations should consider more advanced technologies such as multispectral imaging (MSI) readers.
With the simple touch of a finger, biometrics empower a wide range of use cases across multiple industry sectors ranging from banking and finance, retail, healthcare to government and law enforcement.
As industries evolve their identity and access strategies, they face unprecedented threats and challenges from fraud, account takeover and impersonation. Fingerprint biometrics continue to offer the most accurate, efficient and secure solution that addresses real-world challenges faced by enterprises today.

