
Cost containment strategy: Strengthening enterprise security
We are living in uncertain times. Most economists predict that the global economy will continue to slow this year, and the APAC region certainly isn't bucking this trend. Between supply chain issues, mass layoffs, high inflation, and high-interest rates, it is no surprise that we are seeing a cautious approach from most companies and industries – strategies, growth plans, and budgets are being rapidly revised.
Since technology investments typically take a large chunk out of an organisation's budget, many leaders are trying to navigate these uncertainties and challenges through cost containment measures in the IT division – namely, cutting budgets, reducing discretionary spending, and suspending ongoing projects and initiatives. However, one must be cautious with such cuts as the rise in cybersecurity breaches resulting in loss of data, customers, revenue, and reputation, show no sign of slowing down.
CIOs are under tremendous pressure to find innovative ways to help organisations contain costs efficiently and effectively while simultaneously taking action to harden their enterprise security postures. Faced with such a dilemma, many organisations take a piecemeal approach to cost containment by deploying initiatives in BAU at a tactical level. It is rare for such a method to deliver the required results. What's needed is an integrated, holistic approach where cost containment is supported by strategic investment.
An integrated approach to cost containment
Effective cost containment involves the systematic reduction of costs without impacting overall business operations and resulting in year-on-year savings. This is achieved through establishing a Cost Transparency Model followed by rationalisation and optimisation.
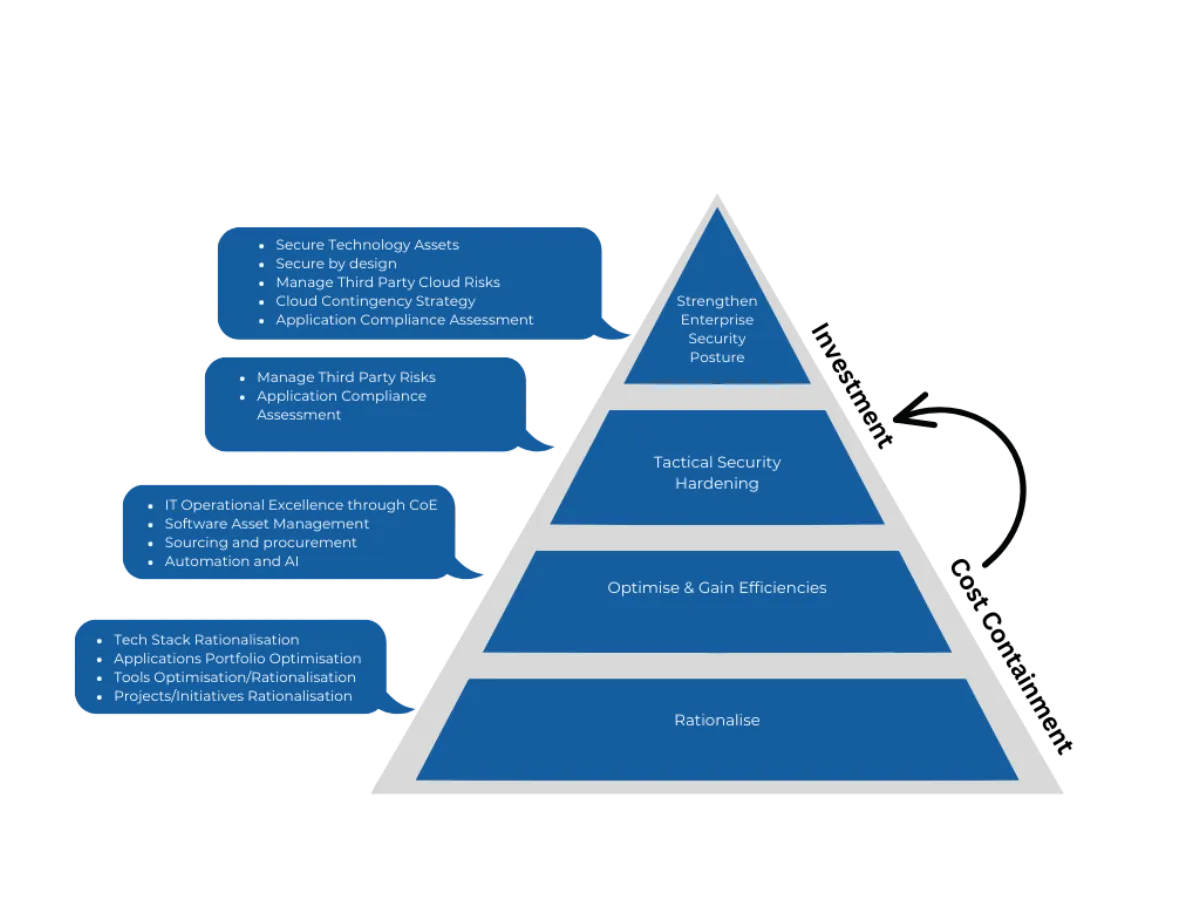
1. Cost Transparency Model: This is a critical foundational element to establish a data-derived, fact-based, current-state view of the organisation's IT CAPEX and OPEX costs. Through a value management framework such as TBM, an IT general ledger and associated cost pools can be defined and managed as an organisation embarks on its cost-containment journey.
2. Rationalisation: Most medium and large organisations have tremendous potential for rationalisation, which aims to identify redundancies and bring about cost efficiencies that can be applied across many domains, including:
a. Infrastructure rationalisation
b. Applications rationalisation and decommissioning
c. Tool and license rationalisation
d. Project and initiative rationalisation
3. Unlocking efficiencies at scale and accelerating growth: Building an AI-first core can help CIOs further expand their cost containment horizon. An AI-first strategy helps organisations gain efficiencies across people, processes, and technology by using key levers such as:
- IT operational model optimisation
- Application portfolio management
- Optimisation of sourcing and procurement functions
- Implementation of automation and AI and other capabilities
Infosys' AI first offering, Infosys Topaz, can help enterprises accelerate growth by building connected ecosystems and unlocking efficiencies at scale.
Building a Stronger Enterprise Security Posture
The next part of the integrated strategy is about strengthening the enterprise security posture. Several trends have compounded the acceleration of cyberattacks in recent times. These include work-from-home culture, bring-your-own-device practices, the increasing adoption of cloud and other digital channels and technologies, and complex social, economic, and geopolitical factors.
Unfortunately, this means that it's unlikely we'll see a decline in cyberattacks for some time, and investment in security will continue to be critical. At a high level, such an investment strategy could be completed in two stages:
1. Immediate security hardening: CIOs focus on cost avoidance by leveraging immediate security hardening measures to address vulnerable assets with known risk profiles, alleviating immediate security concerns by:
a. Managing third-party security risks
b. Carrying out an application compliance assessment
2. Strengthening enterprise security posture: The year-on-year savings generated from the above cost containment initiatives can help the organisation to self-fund the fortification of its strategic, holistic, enterprise-wide security plan. For this, steps can be taken to:
a. Secure technology assets
b. Build zero-trust architecture
c. Manage cloud security risks
d. Conduct application compliance assessment
For those looking to strengthen their enterprise security posture, it would be worth connecting with various customer-centric divisions of their business. These areas are likely to provide valuable insights into consumer trends and behaviours that create potential security concerns. The public (and their current and potential customers) today is more aware and concerned about cybersecurity than ever before, we, therefore, foresee an organisation's commitment to security becoming a key market differentiator in the near future.
In order to survive and thrive in these uncertain times, CIOs must come up with an innovative and holistic enterprise-wide cost containment strategy – significant cost reduction simply cannot be achieved at a tactical level. By funnelling some of these savings into enterprise cyber security, CIOs can mitigate the ever-increasing and evolving risks their organisations face. If done strategically, such investments may not only strengthen an organisation's security posture but its customer retention, attraction, and overall brand equity as well.

