
Where does a malware analysis sandbox fit in your cybersecurity strategy?
Malware analysis sandboxes offer a comprehensive approach to malware analysis, encompassing both static and dynamic techniques. This comprehensive evaluation provides a more holistic understanding of the malware's capabilities and potential impact. However, many organizations face challenges in determining the most effective way to implement a sandbox within their security infrastructure. Let's examine some common scenarios where a sandboxing solution can be utilized effectively.
What is a Malware Analysis Sandbox?
A malware analysis sandbox is a software application or virtual environment that isolates and analyzes suspicious files or links. It offers a secure and controlled virtual machine (VM) environment where analysts can safely execute and observe the behaviour of malware without risking infection to their own systems or networks to gain valuable insights into its functionality, tactics, and operations.
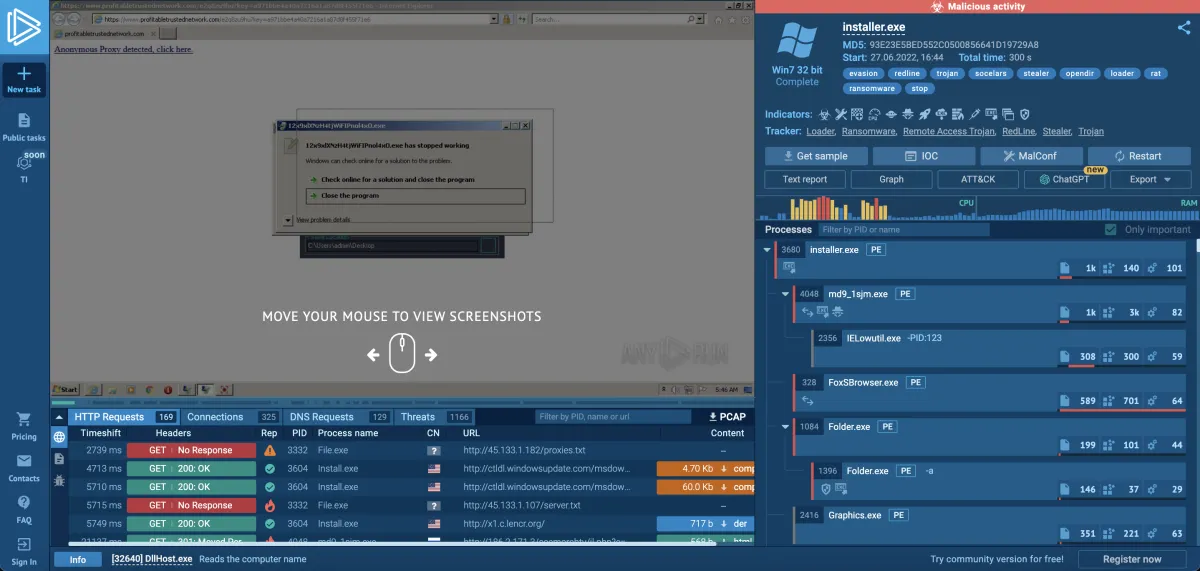
RedLine malware analyzed in the ANY.RUN sandbox
ANY.RUN is a cloud-based malware analysis sandbox that lets you analyze files and links inside fully interactive virtual machines. Try it for 14 days at no cost.
Threat Information Gathering
Sandboxes excel at analyzing malware's behaviour, enabling analysts to monitor how a malware sample interacts with the system and network. They empower professionals to extract knowledge of emerging threats, attack vectors, and malware families.
This capability is crucial for proactive cybersecurity, where organizations must stay ahead of the latest threats emerging in the cyber sphere. By submitting newly found malware samples to a sandbox, analysts can detect and analyze them in real time and collect actionable indicators of compromise (IOCs). These IOCs, such as IP addresses, URLs, and file hashes, can be integrated into security systems to enhance detection capabilities and prevent potential attacks.
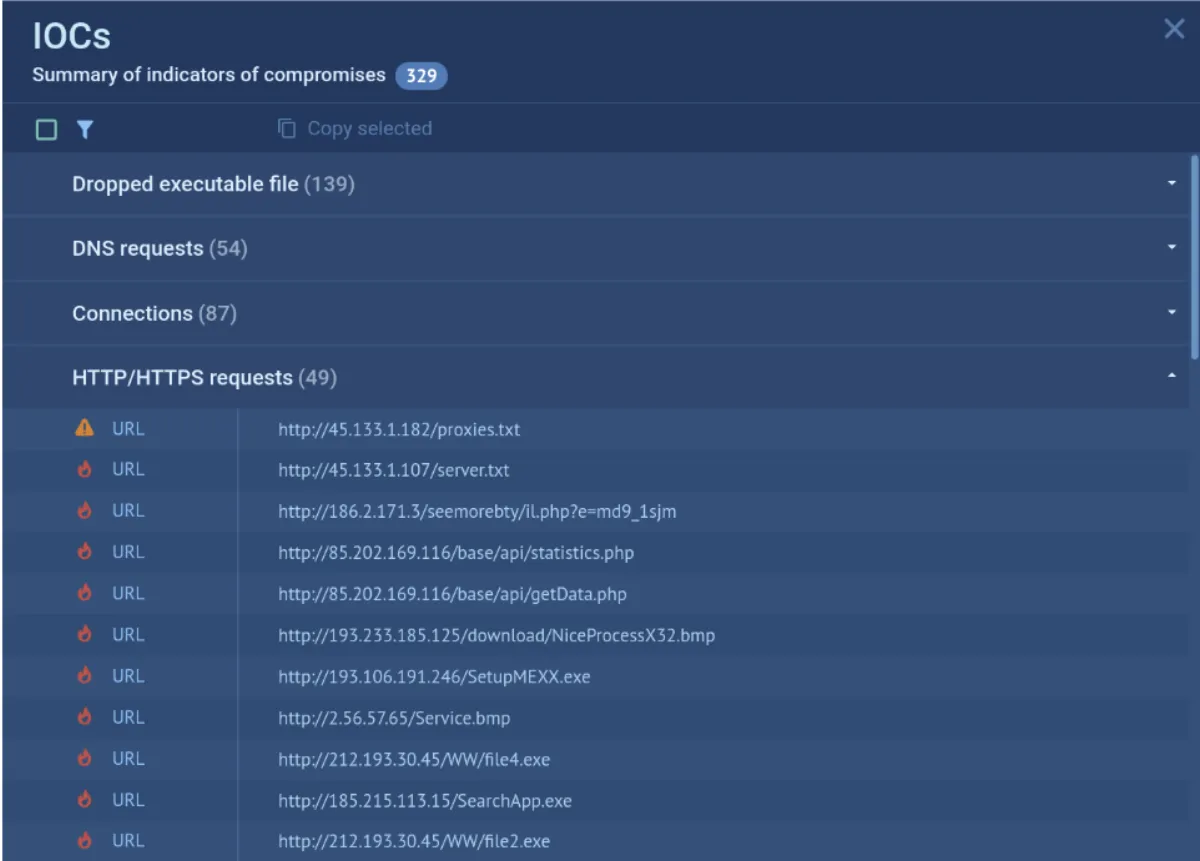
RedLine's IOCs extracted by ANY.RUN
Examination of Suspicious Files and Links
Malware analysis sandboxes are indispensable when it comes to examining suspicious files and links. Phishing emails containing malicious attachments and URLs are the most common attack vector. A sandbox provides analysts with the means to thoroughly examine such content without posing any risk to their own networks.
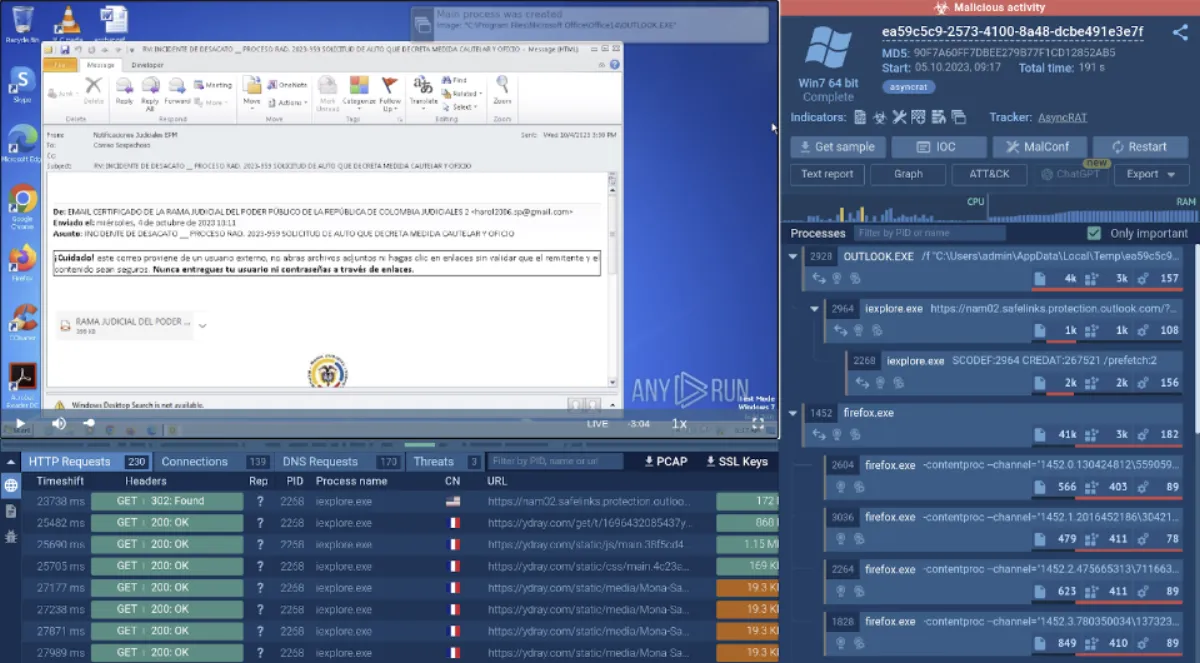
A phishing email opened in ANY.RUN
Moreover, interactive sandboxes like ANY.RUN offers users direct control over the analysis process, enabling them to interact with malware samples as needed. Essentially, it allows users to open files, run programs, and click on links within the VM environment, just like on a standard computer. This hands-on approach allows analysts to gather more details about the file's potential malicious functionality, informing their decision regarding its safety and potential threat level.
The sandbox's ability to analyze suspicious URLs and download and execute files presents a valuable opportunity to identify the tactics, techniques, and procedures (TTPs) employed by cyberattackers. By closely scrutinizing the file's actions and interactions, analysts can gain insights into the attacker's methods and apply appropriate countermeasures to prevent future intrusions.
Investigations into Elusive Malware
Malware often employs sophisticated evasion techniques to circumvent traditional security measures. Sandboxes can effectively detect these evasive tactics by mimicking real-world conditions, including network configurations and user interactions.
Within the sandbox, analysts can observe how the malware attempts to hide its malicious behaviour, such as modifying system settings, disabling security mechanisms, or communicating with command-and-control servers. By identifying these evasion techniques, analysts can gain a deeper understanding of the attacker's methods and apply appropriate countermeasures to prevent future intrusions.
Analysis of Malware's Network Traffic
Analyzing a malicious software's network communication is a critical step in malware research. Sandboxes simplify and enhance this process by providing analysts with the right tools for different situations.
For instance, ANY.RUN can intercept and decrypt encrypted traffic, allowing analysts to see what data is being exchanged between the malware and its command-and-control (C2) servers.
Additionally, sandboxes are essential for analyzing malware that targets specific geographic regions. By configuring the sandboxed VM to have the desired IP address and language settings, and activating a residential proxy, analysts can disguise the sandbox environment, bypass the malware's evasion techniques, and effectively study its malicious activities.
Embrace the Cloud-Based ANY.RUN Malware Analysis Sandbox
Experience the power of the cloud-based ANY.RUN malware analysis sandbox and witness how it can strengthen your cybersecurity posture. With fully interactive virtual machines, support for all popular Windows versions, and API integration, you can streamline your threat investigations and quickly determine if a file or link is malicious.
Request a 14-day free trial to explore all features of ANY.RUN.

