Why ClickFix attacks are outpacing enterprise security
In January, a multinational manufacturing firm discovered that attackers had accessed their network for 47 days. The entry point was a single PowerShell command executed by their Director of Operations. The attack vector wasn't an elaborate zero-day exploit, but a ClickFix campaign – a technique that emerged just a year ago and has now become the preferred method for everyone from opportunistic cybercriminals to nation-state actors.
ClickFix has been used to deploy various malware, including: Remote Access Trojans (AsyncRAT, NetSupport RAT), banking malware (Danabot), information stealers (Lumma Stealer), Post-exploitation frameworks (Havoc C2) and other malware including DarkGate, SectopRAT, and XWorm. By March 2025, ClickFix attacks had become more sophisticated, with new campaigns discovered using the technique to deploy the Havoc post-exploitation framework via Microsoft SharePoint.
Each successful attack creates multiple potential impact vectors: data exfiltration, ransomware deployment, cryptocurrency mining, or establishing persistent access for future operations.
Why ClickFix attacks are spreading like wildfire
Since its first documented use in March 2024, ClickFix has rapidly transformed from a novel tactic to one of the most effective attack vectors in the current threat landscape. There are several structural factors driving its effectiveness:
1. Exploiting the gap between human and machine
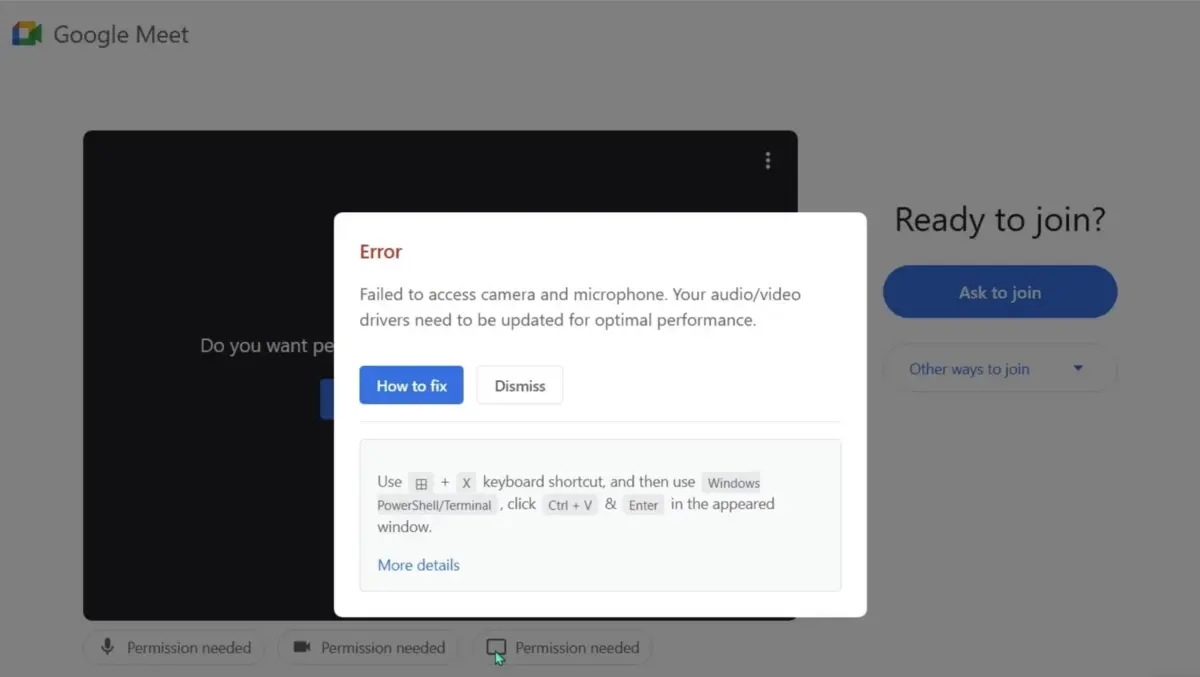
ClickFix attacks operate at the precise intersection where technical controls end and human judgment begins. Rather than attempting to exploit software vulnerabilities, these attacks present convincing error messages or verification prompts that lead users to voluntarily execute PowerShell commands. Even security-trained employees execute these commands at concerning rates when presented with contextually relevant scenarios.
2. The browser security blind spot
Current enterprise security architecture maintains a critical blind spot that ClickFix specifically targets. Modern security tools struggle with browser-based threats due to structural reasons:
- Endpoint detection and response limitations: EDR tools typically monitor system-level activities but lack visibility into the browser rendering engines where ClickFix operates. When a user copies and pastes a command from a browser into PowerShell, EDR has no idea to the context that the copy was initiated on.
- Secure web gateways limitations: SWGs inspect traffic but cannot analyze the client-side social engineering where Powershell scripts are copied to user's clipboard. ClickFix does not rely on any file download through the browser, making it more insidious and blind to the Secure Web Gateway.
3. Technical accessibility drives adoption
The barrier to entry for launching effective ClickFix campaigns has dropped precipitously. Open-source frameworks and modified phishing kits now incorporate ClickFix templates, creating an unprecedented democratization of this attack technique.
ClickFix attacks highlight a structural gap in current defense strategies. Traditional security models built around perimeter protection and network monitoring have fundamental limitations against browser-centric threats that operate where users spend 80 percent of their digital workday.
Addressing the ClickFix challenge requires security that operates within the same context as the threat. Browser native security solution approaches offer distinct advantages:
- Contextual analysis: Operating within the browser environment provides full visibility into the rendering, script execution, and user interaction context that initiates ClickFix attacks
- Preventive intervention: Rather than detecting malicious PowerShell after execution, browser security can identify and neutralize ClickFix elements before they reach the command execution stage
- User experience integration: Security that understands browser context can precisely target interventions, maintaining productivity while blocking specific threat vectors
Examples of browser detection and response (BDR) solutions protecting against ClickFix attacks: https://www.youtube.com/playlist?list=PL9E-Z6c21SVhUef8OgrSl-LiBWendSMg7
Strategic imperatives for security leadership
The rapid evolution of ClickFix and similar browser-based attacks signals a fundamental shift in the attack surface that requires equivalent adaptation in defense strategy. The browser has transitioned from just another application to become the primary work environment for most employees and consequently the focal point for sophisticated attacks.
Organizations that implement browser native security as a core element of their defense strategy will significantly reduce their vulnerability to current and future social engineering techniques.

